JumpCloud SCIM provisioning is a paid feature.If you’re using Infisical Cloud, then it is available under the Enterprise Tier. If you’re self-hosting Infisical,
then you should contact sales@infisical.com to purchase an enterprise license to use it.
Create a SCIM token in Infisical
In Infisical, head to your Organization Settings > Authentication > SCIM Configuration and
press the Enable SCIM provisioning toggle to allow JumpCloud to provision/deprovision users and user groups for your organization.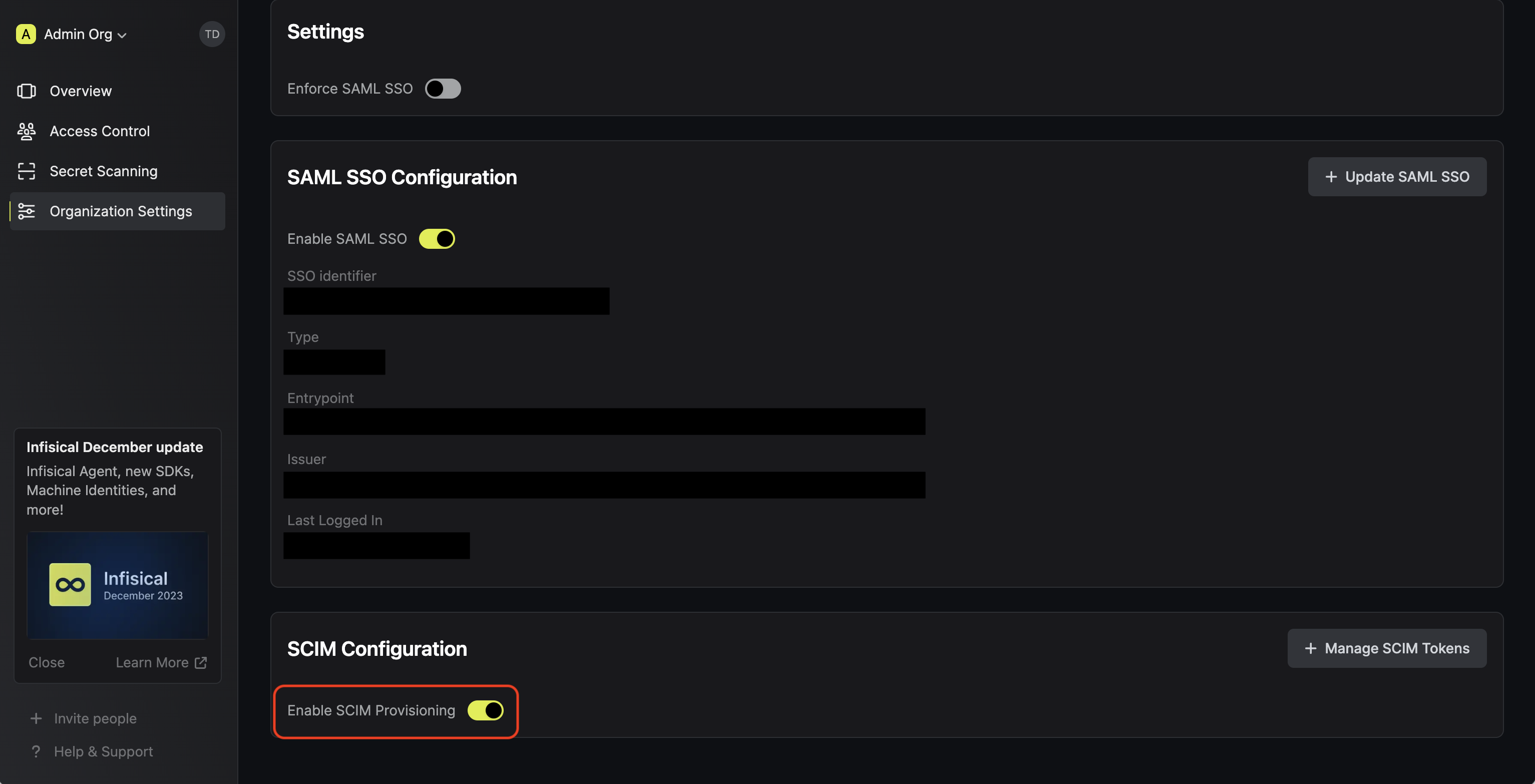 Next, press Manage SCIM Tokens and then Create to generate a SCIM token for JumpCloud.
Next, press Manage SCIM Tokens and then Create to generate a SCIM token for JumpCloud.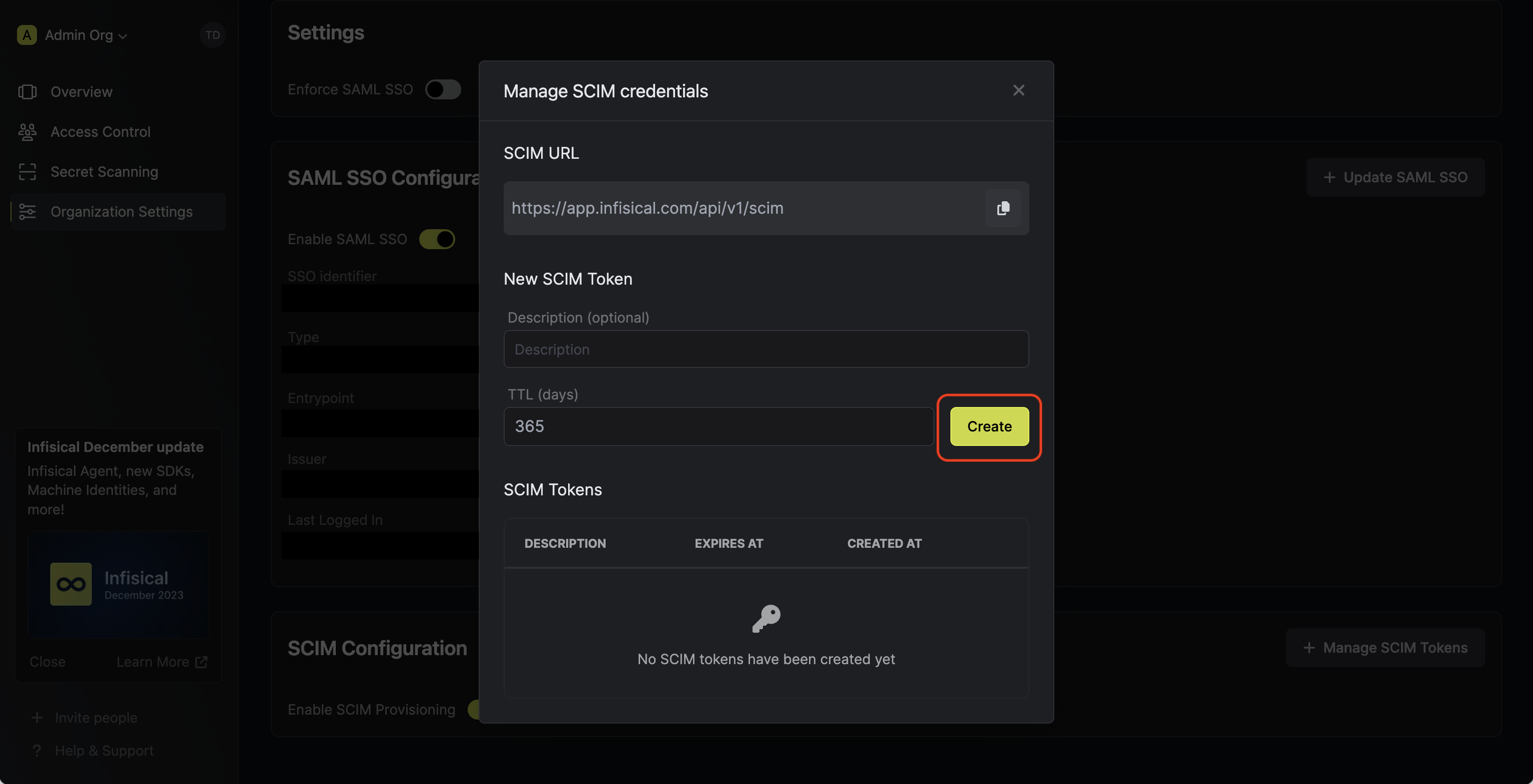 Next, copy the SCIM URL and New SCIM Token to use when configuring SCIM in JumpCloud.
Next, copy the SCIM URL and New SCIM Token to use when configuring SCIM in JumpCloud.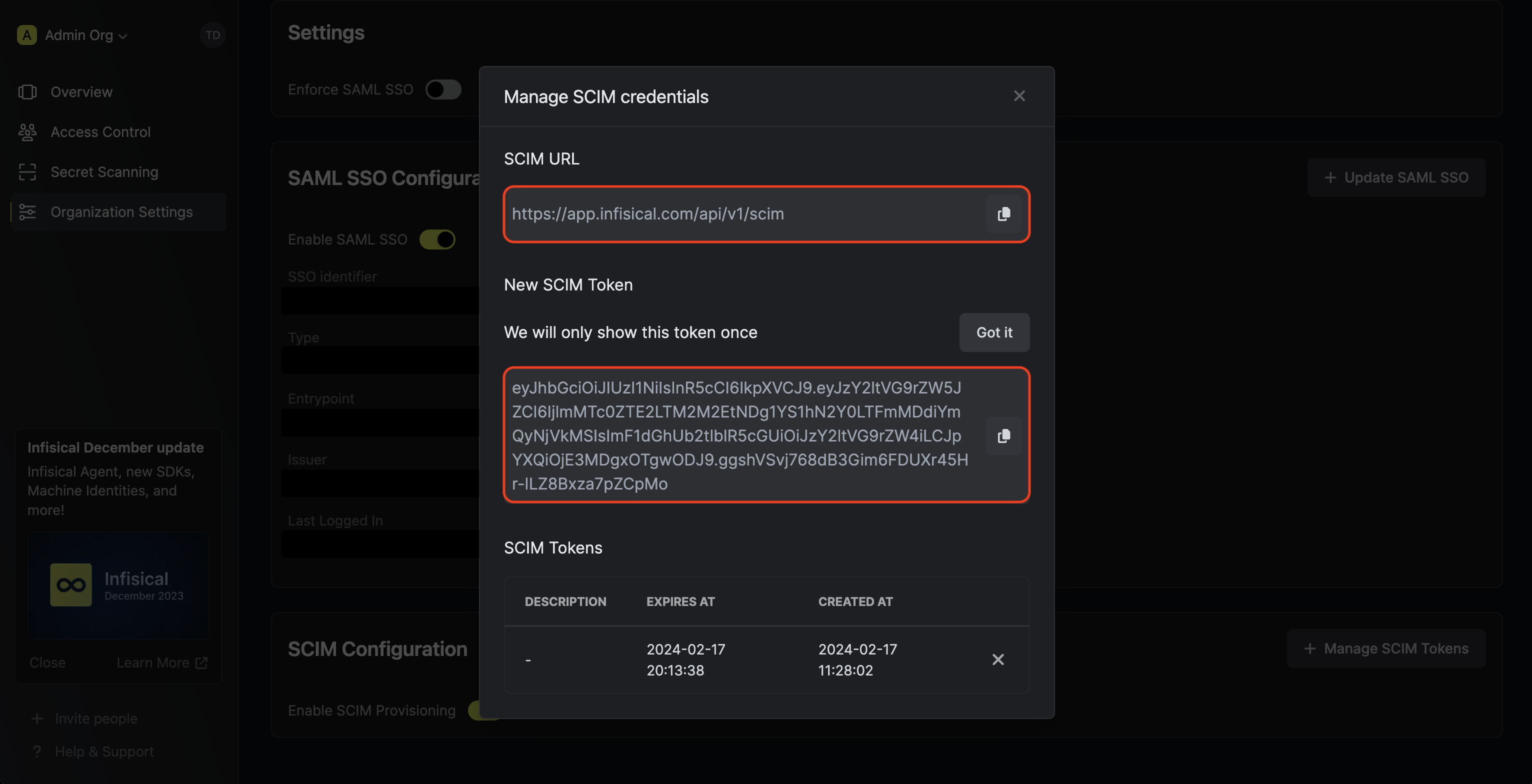
 Next, press Manage SCIM Tokens and then Create to generate a SCIM token for JumpCloud.
Next, press Manage SCIM Tokens and then Create to generate a SCIM token for JumpCloud. Next, copy the SCIM URL and New SCIM Token to use when configuring SCIM in JumpCloud.
Next, copy the SCIM URL and New SCIM Token to use when configuring SCIM in JumpCloud.
Configure SCIM in JumpCloud
In JumpCloud, head to your Application > Identity Management > Configuration settings and make sure that
API Type is set to SCIM API and SCIM Version is set to SCIM 2.0.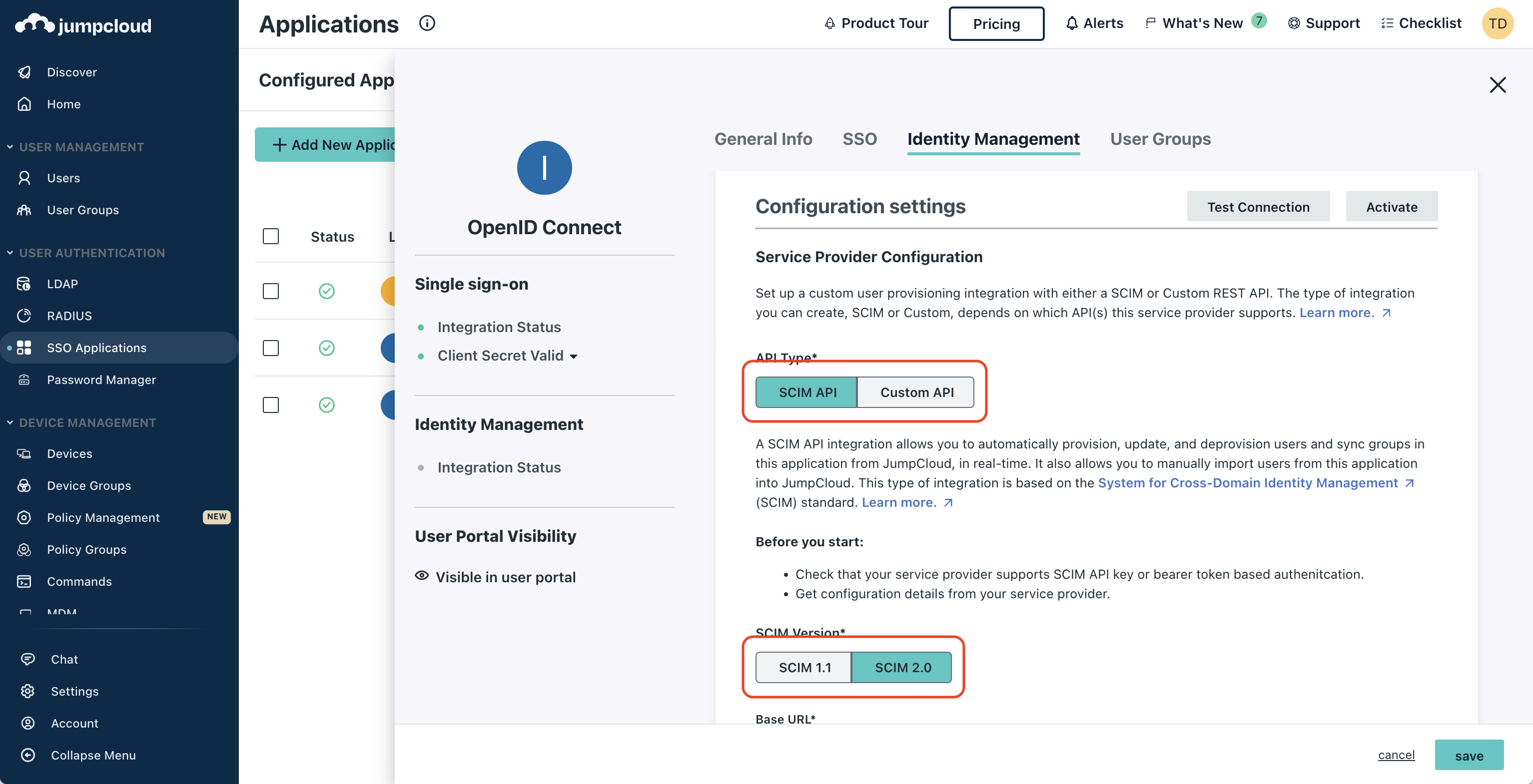 Next, set the following SCIM connection fields:
Next, set the following SCIM connection fields: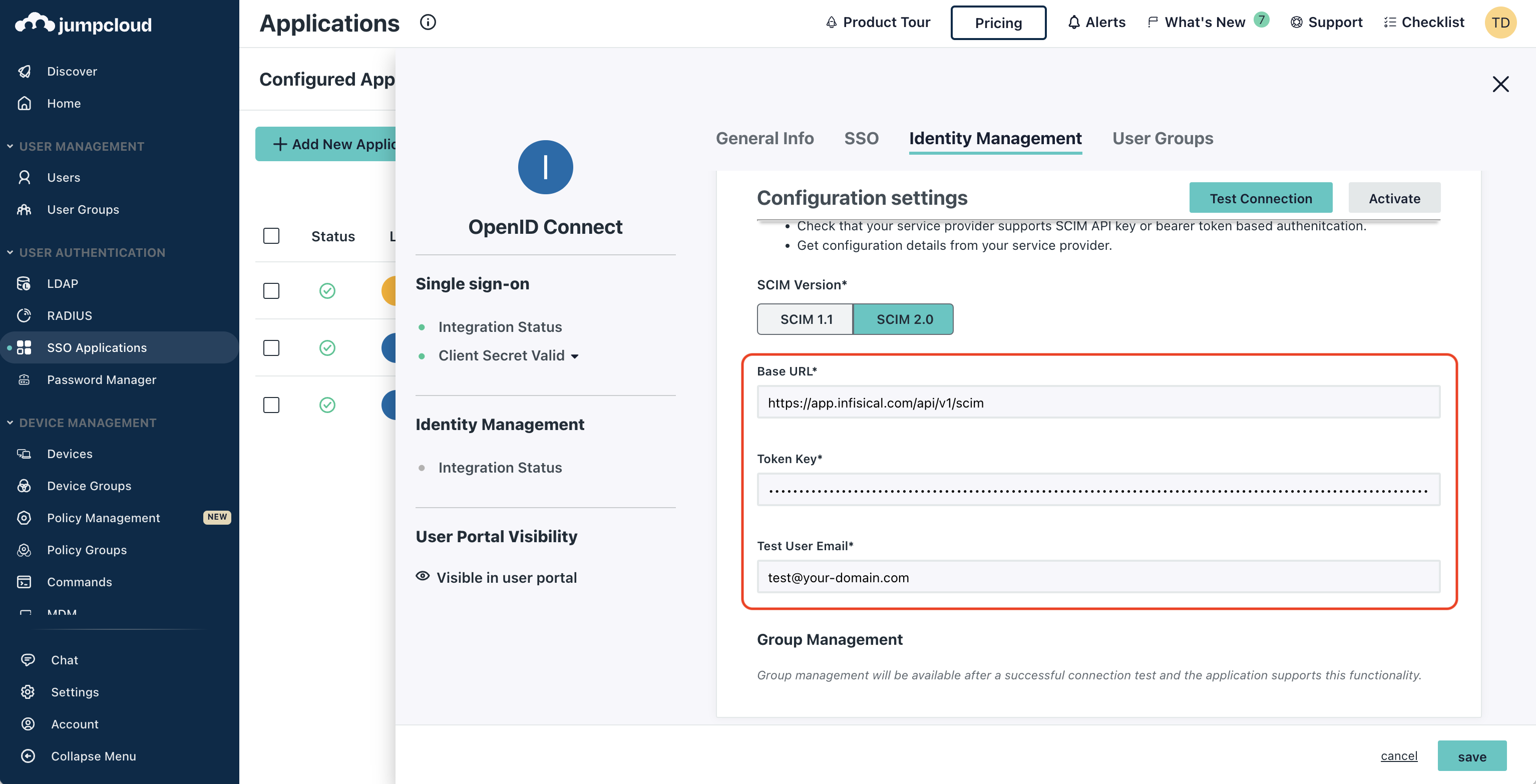 Next, press Test Connection to check that SCIM is configured properly. Finally, press Activate
to have JumpCloud start provisioning/deprovisioning users to Infisical.
Next, press Test Connection to check that SCIM is configured properly. Finally, press Activate
to have JumpCloud start provisioning/deprovisioning users to Infisical. Now JumpCloud can provision/deprovision users and user groups to/from your organization in Infisical.
Now JumpCloud can provision/deprovision users and user groups to/from your organization in Infisical.
 Next, set the following SCIM connection fields:
Next, set the following SCIM connection fields:- Base URL: Input the SCIM URL from Step 1.
- Token Key: Input the New SCIM Token from Step 1.
- Test User Email: Input a test user email to be used by JumpCloud for testing the SCIM connection.
 Next, press Test Connection to check that SCIM is configured properly. Finally, press Activate
to have JumpCloud start provisioning/deprovisioning users to Infisical.
Next, press Test Connection to check that SCIM is configured properly. Finally, press Activate
to have JumpCloud start provisioning/deprovisioning users to Infisical. Now JumpCloud can provision/deprovision users and user groups to/from your organization in Infisical.
Now JumpCloud can provision/deprovision users and user groups to/from your organization in Infisical.Why do SCIM-provisioned users have to finish setting up their account?
Why do SCIM-provisioned users have to finish setting up their account?
Infisical’s SCIM implmentation accounts for retaining the end-to-end encrypted architecture of Infisical because we decouple the authentication and decryption steps in the platform.For this reason, SCIM-provisioned users are initialized but must finish setting up their account when logging in the first time by creating a master encryption/decryption key. With this implementation, IdPs and SCIM providers cannot and will not have access to the decryption key needed to decrypt your secrets.

